


Ghidra is an open source and free reverse engineering application developed by National Security Agency(NSA) which is available on all the platforms i.e Mac,Linux,Windows. The binaries were released at RSA Conference in the year 2019 in March; the sources were published after a month on GitHub. Ghidra is seen by many pentesters as a competitor to IDA Pro. The source code is completely available for download at ghidra-sre.org along with the latest 9.1.1 patch.
It helps pen testers to analyze malicious code and various types of malware like viruses and has given pen testers a better understanding of potential vulnerabilities in their networks and applications. Has an arsenal of software analysis tools for analyzing fully compiled code on various platforms including Windows, Mac OS, and Linux.
Key features include:
1. Disassembly
2. Assembly
3. Decompilation
4. Graphing and scripting
multiple other features that support a wide variety of processor instruction sets and executable formats that can run in both user-interactive and system automated modes.
Pentesters develop their own Ghidra plug-in components and scripts using the exposed API in Ghidra.
To install Ghidra you need to download the main Ghidra zip file from Here
After the download is complete extract the zip file and go to the directory where the file is extracted.
Open Command line/Terminal in this directory and run this command.
#./ghidraRun

That completes the process of installation.
To test an application we are going to take the infamous WannaCry Ransomeware’s malware.
You can download the malware from here:
https://www.ghidra.ninja/samples/wannacry.zip
Password : ghidra.ninja
(Ps: Do not install this on your windows system at all if you wanna see how it works test it on a windows virtual machine)
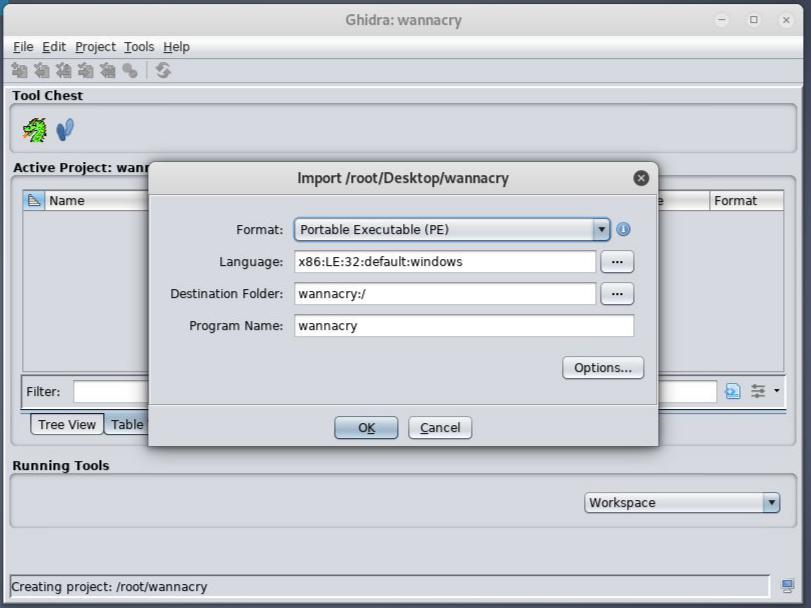
After you have downloaded and extracted the wannacry malware then just go ahead and drag and drop the any.exe file in Ghidra after creating a project.
You need to install one more application i.e. WRESTOOL Just type #apt install icoutils in your kali terminal and it will be installed As it is a part of icoutils pack this tool will be used in future for exploitation.
Now lets start reverse engineering wannacry:
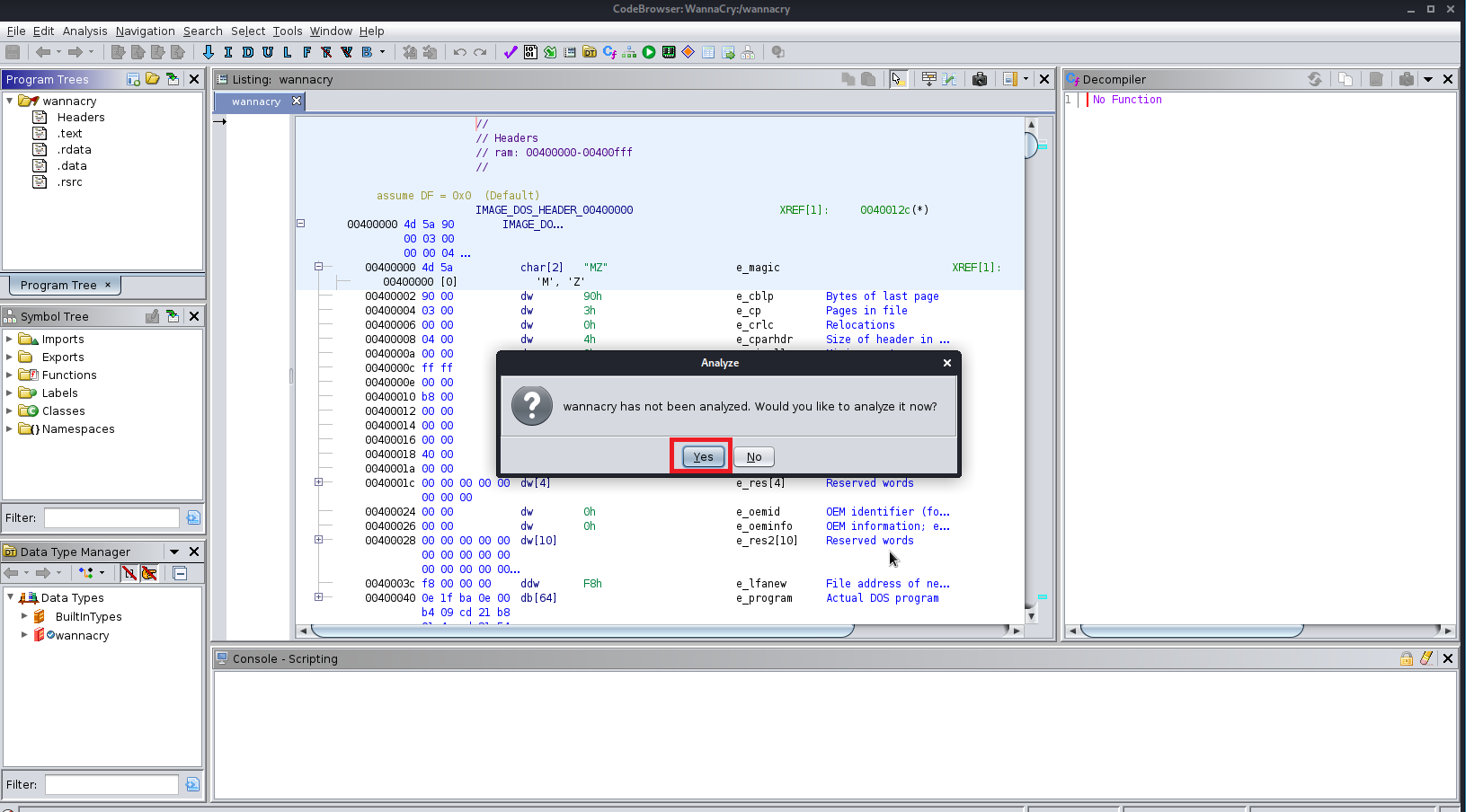
1. First analyze the wannacry file
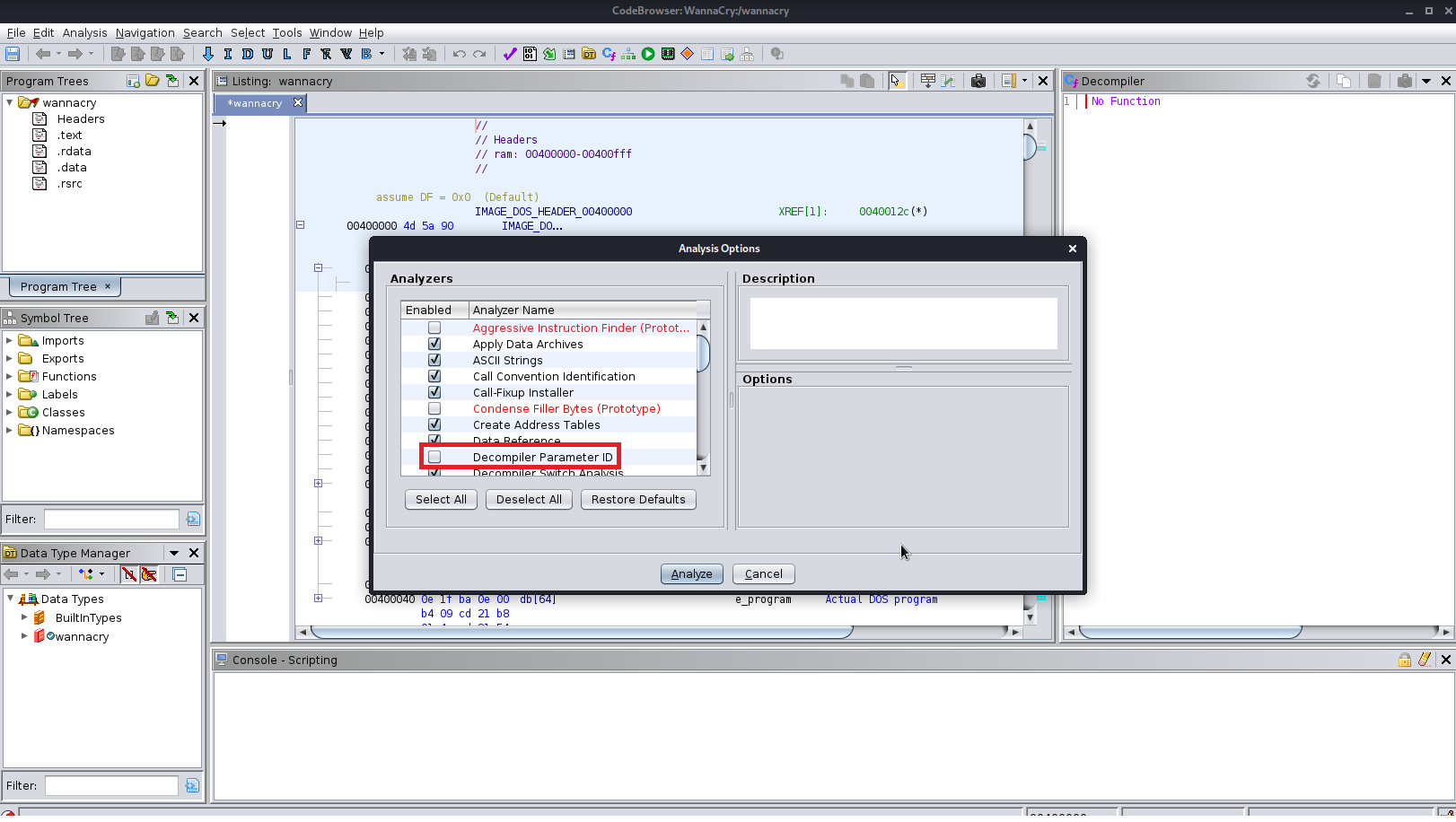
2. Select Decompiler Parameter ID to analyze.
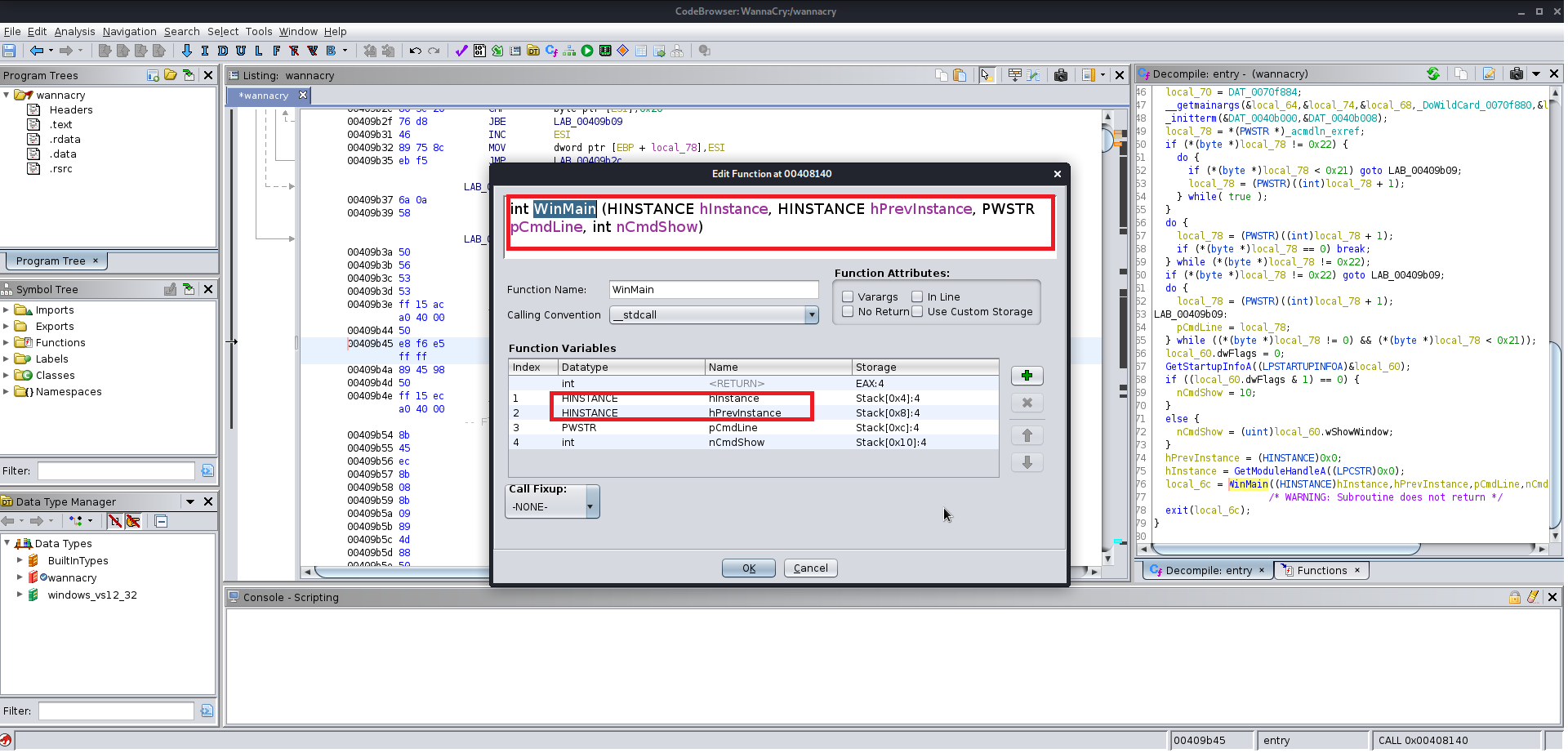
3. After it has been analyzed go to the functions tab and search for entry point.
After finding the entry point just analyze the file manually you will find the this file at the end uses a winmap function which is used by a lot of the windows exe file and you keep analyzing the file you will find a lot of the other function which are supposed to be altered according to you give them the name which you like you will need to change the data type of various functions labels and variables as well because Ghidra does not manage to get all the information from the precompiled wannacry.exe
Here are few images for what I did:
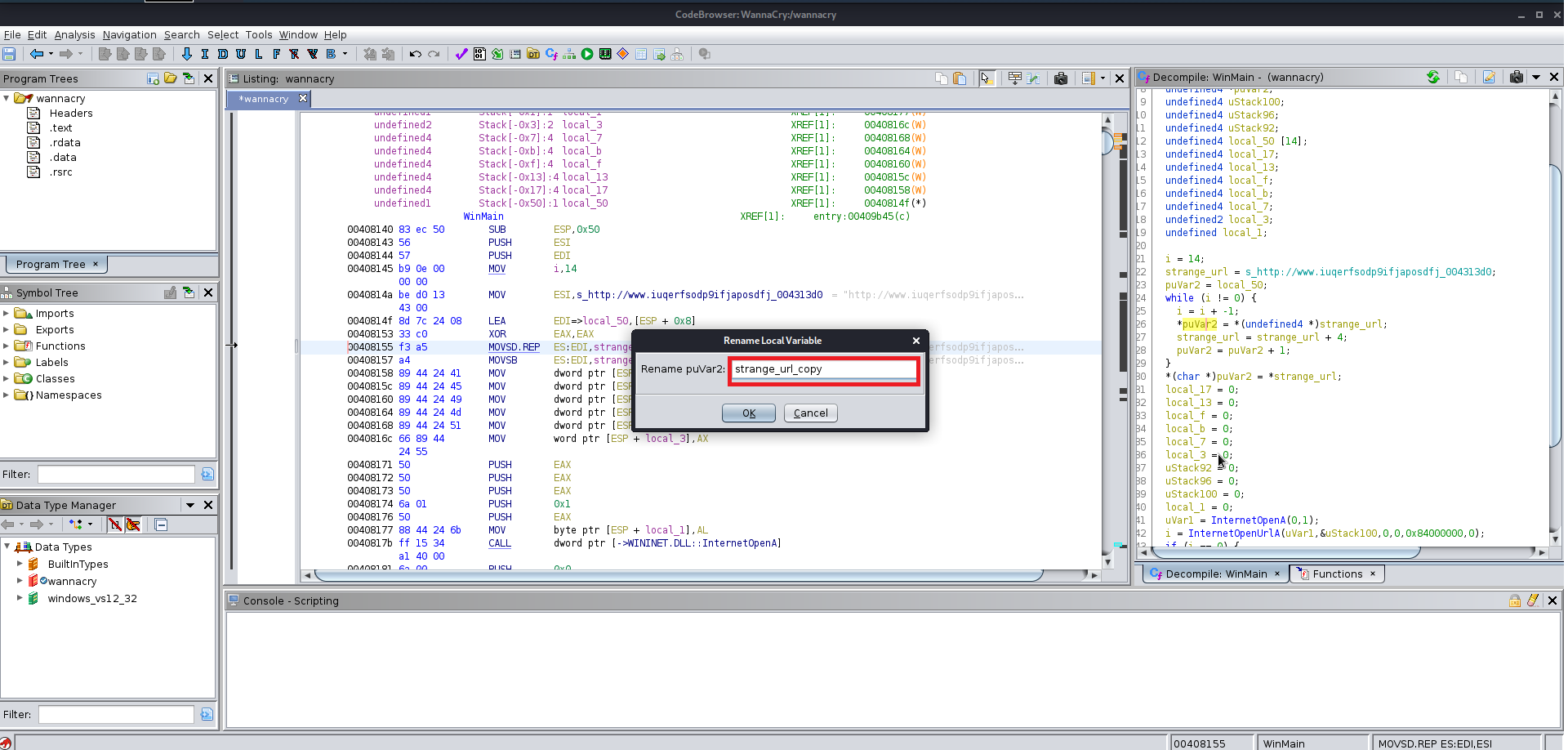
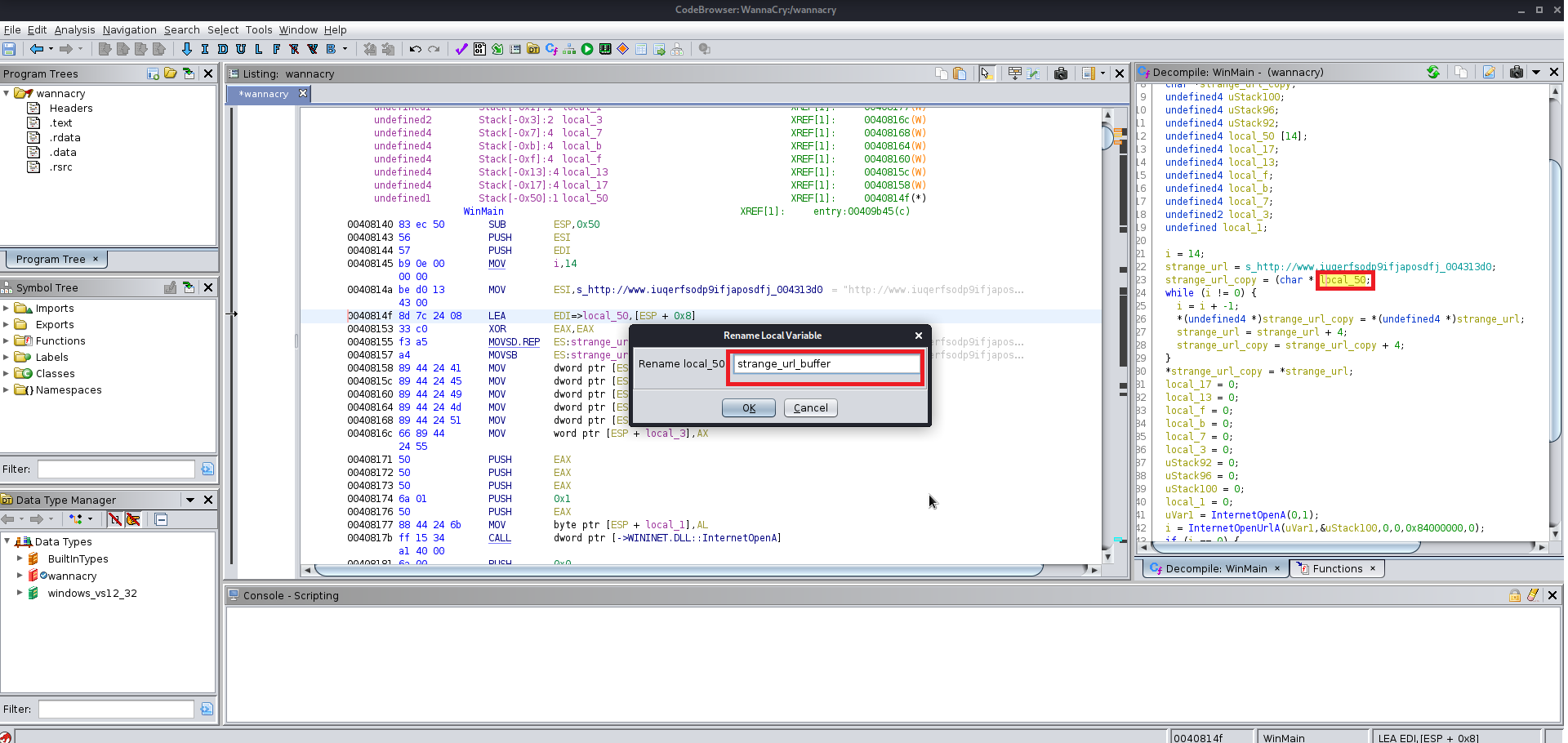
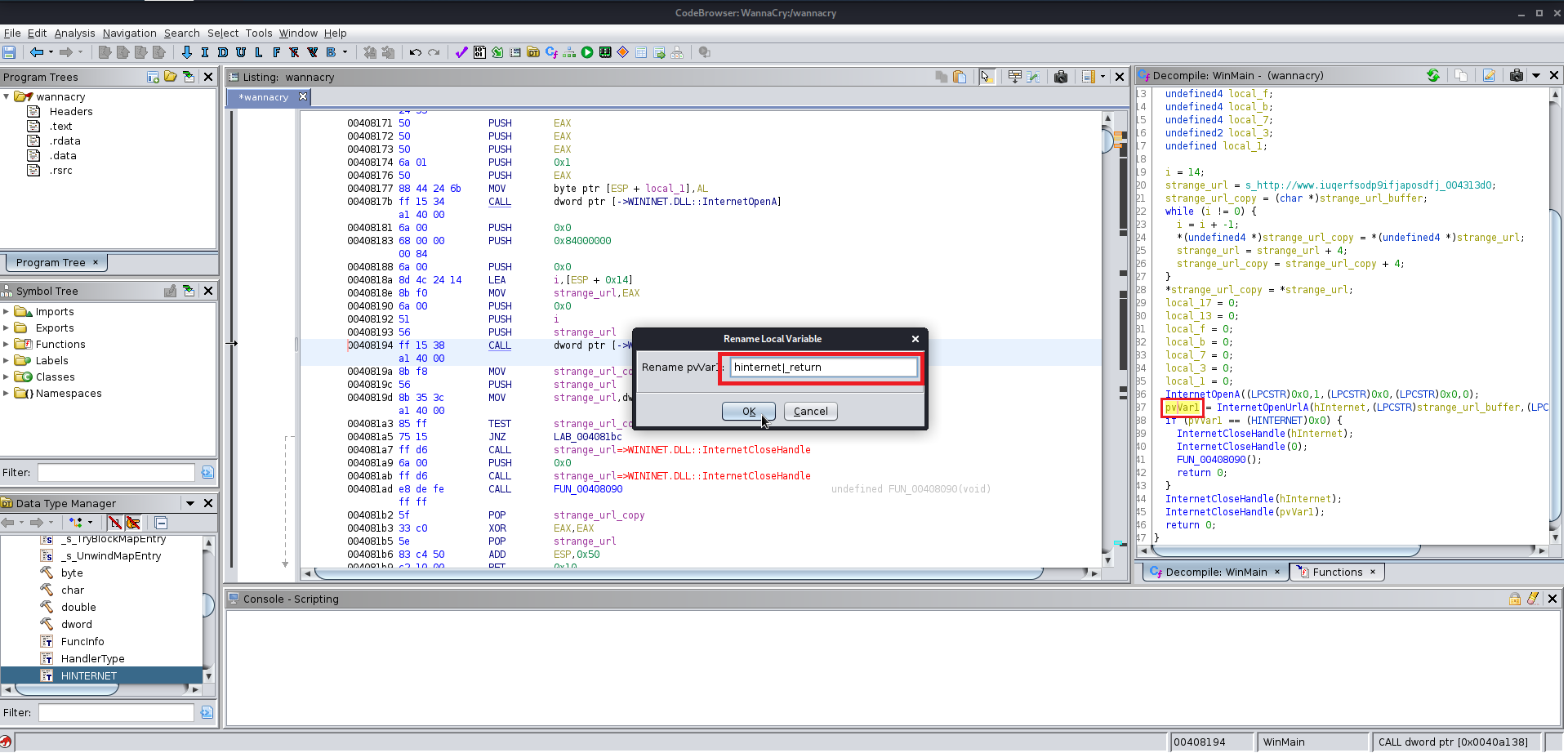
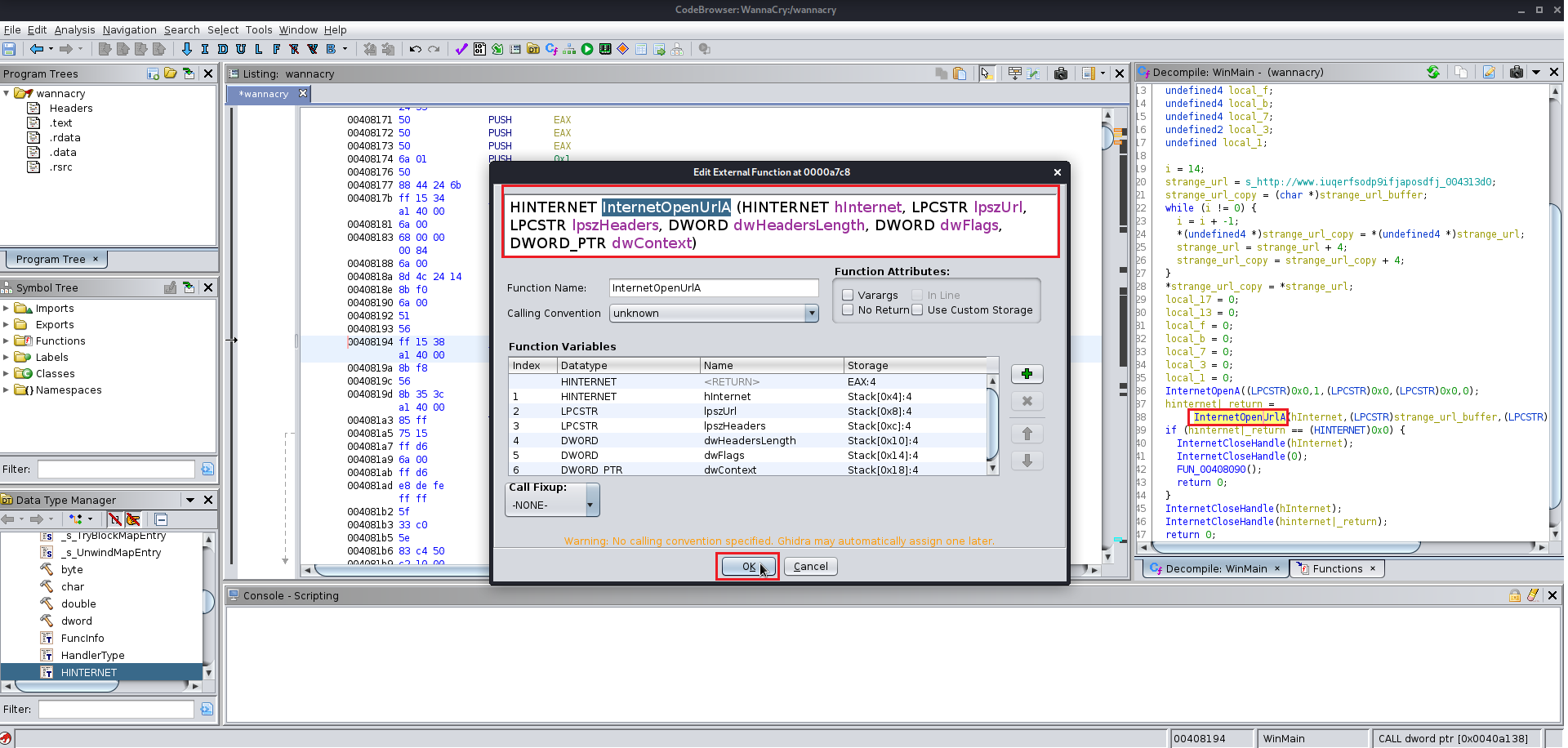
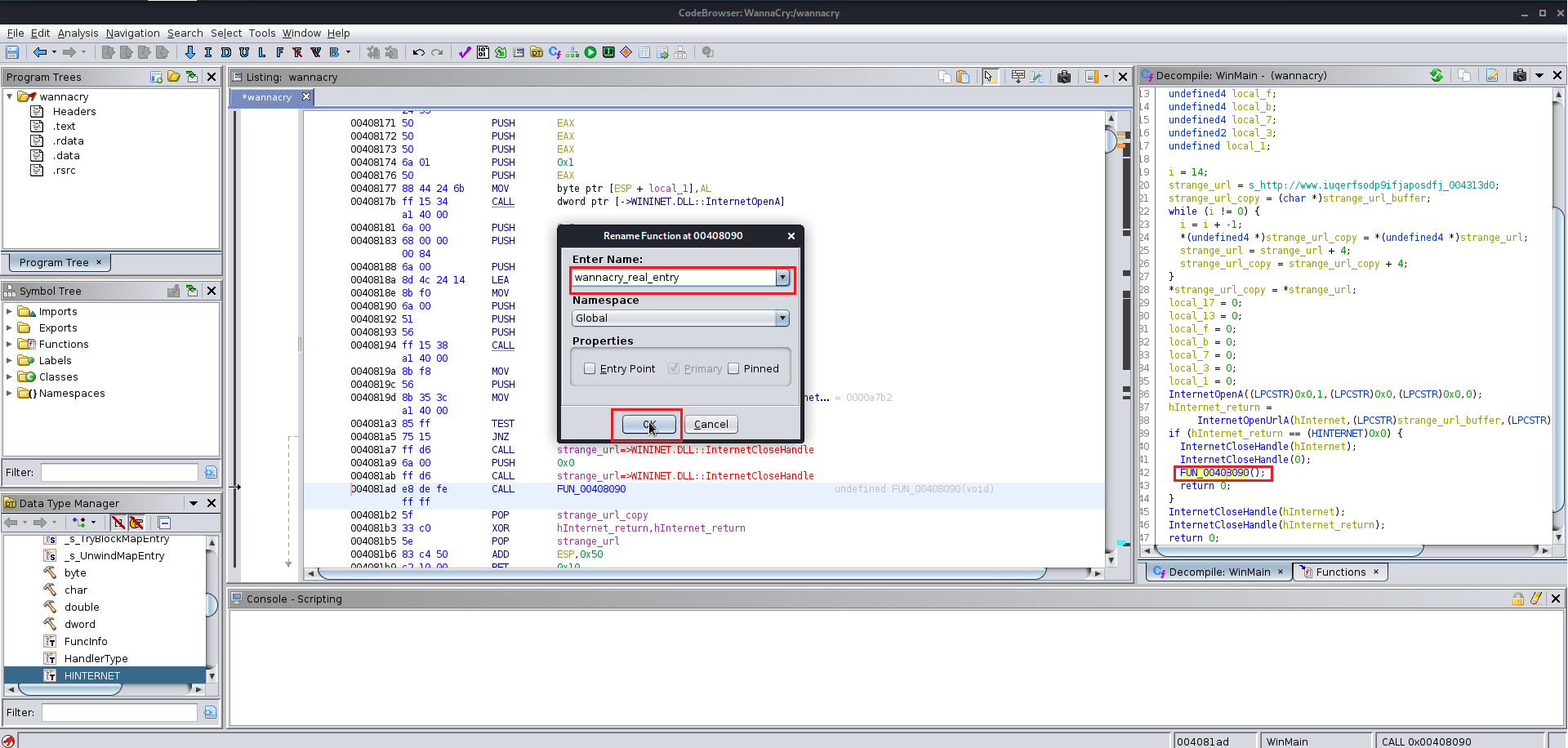
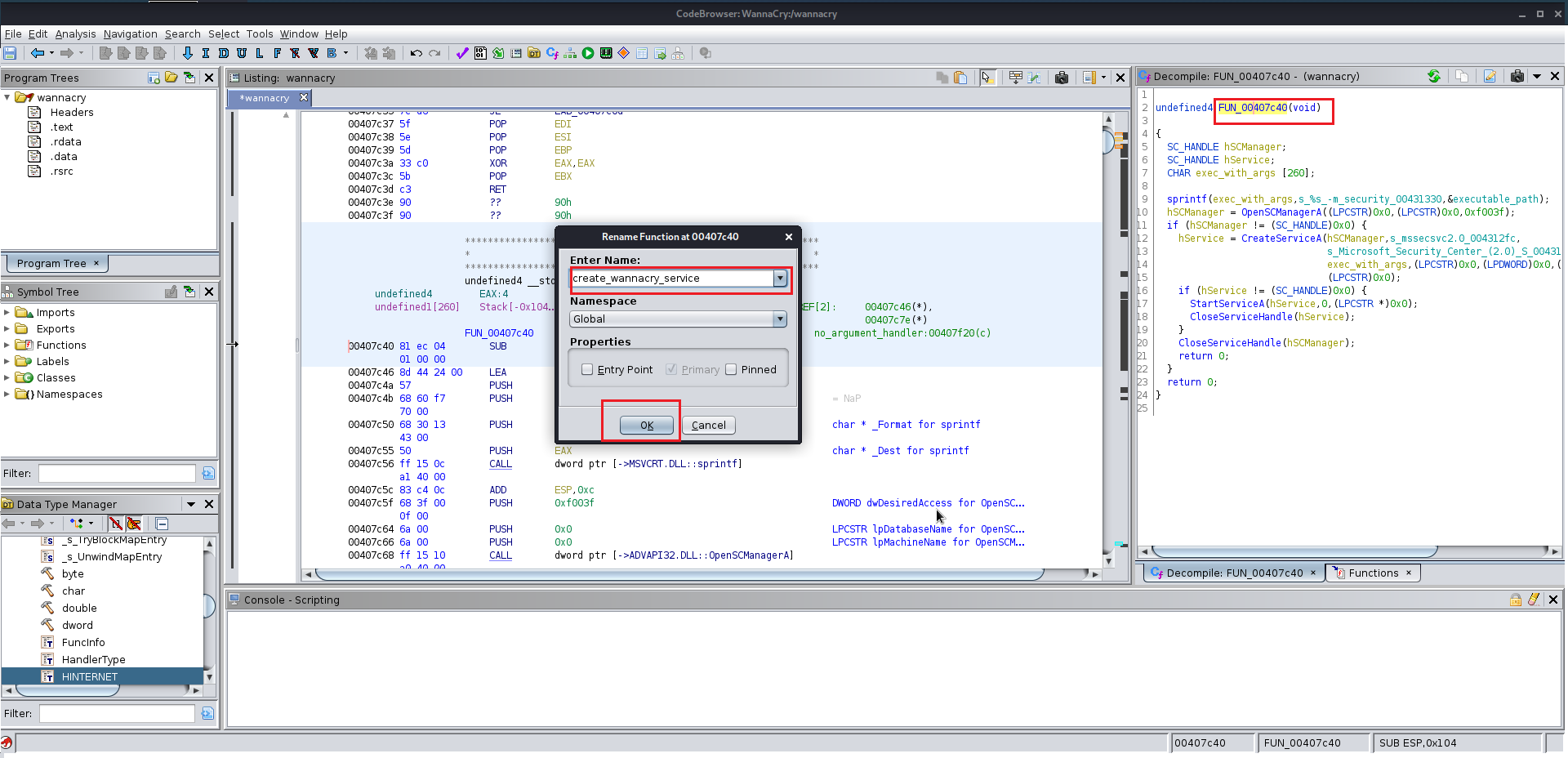
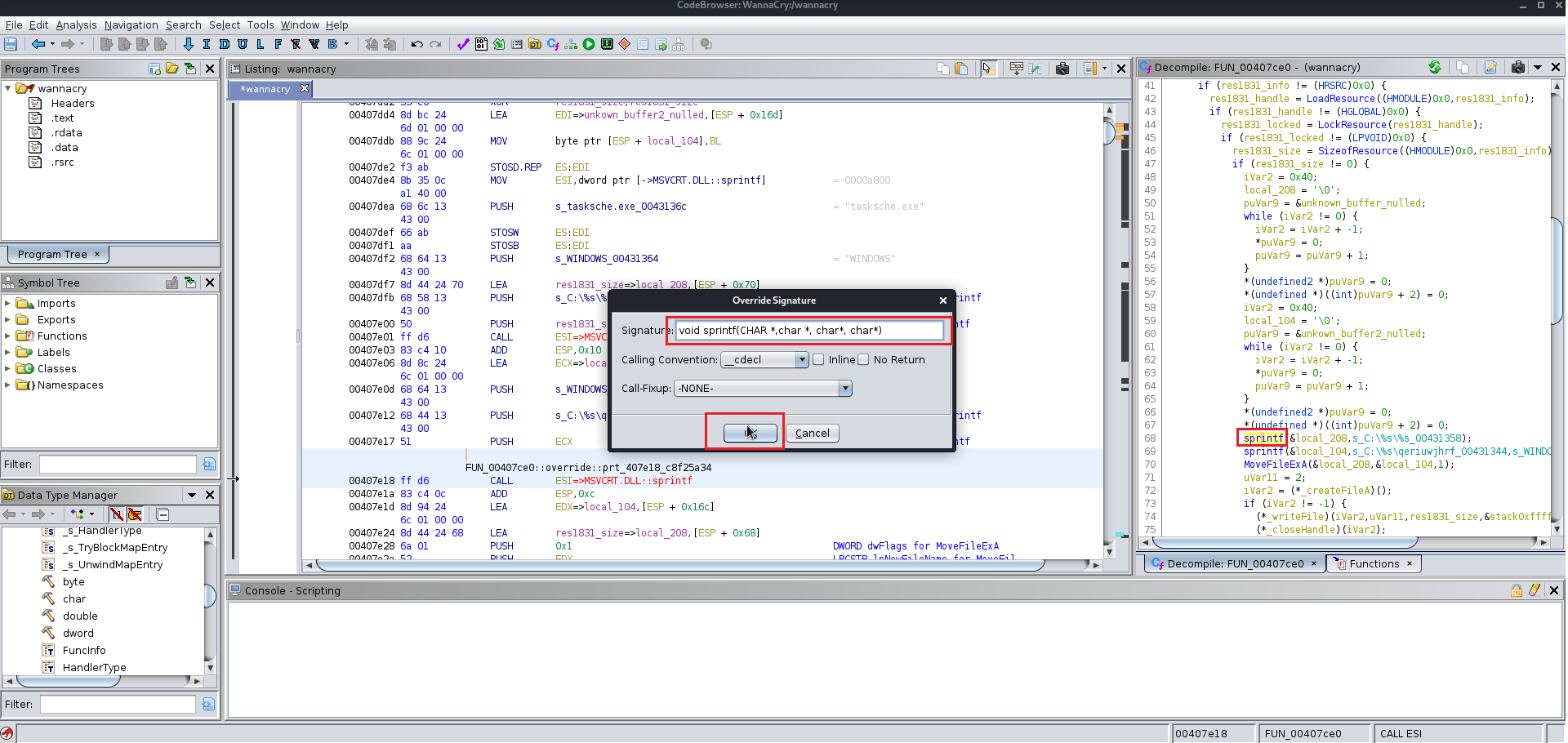
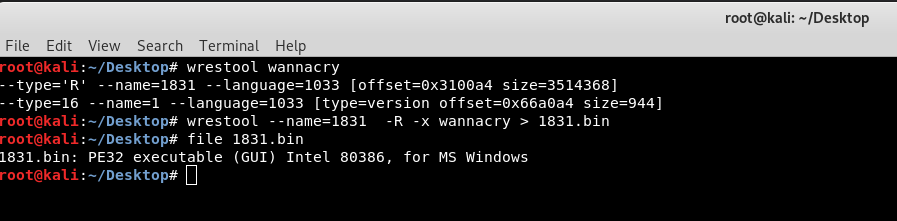
Now we need the wrestool :
Just type in the terminal : wrestool wannacry
It will give you an output like this:
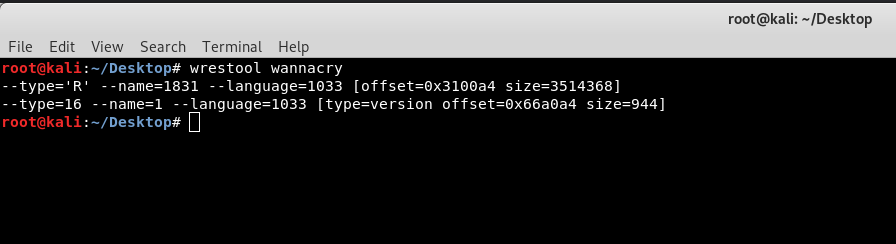
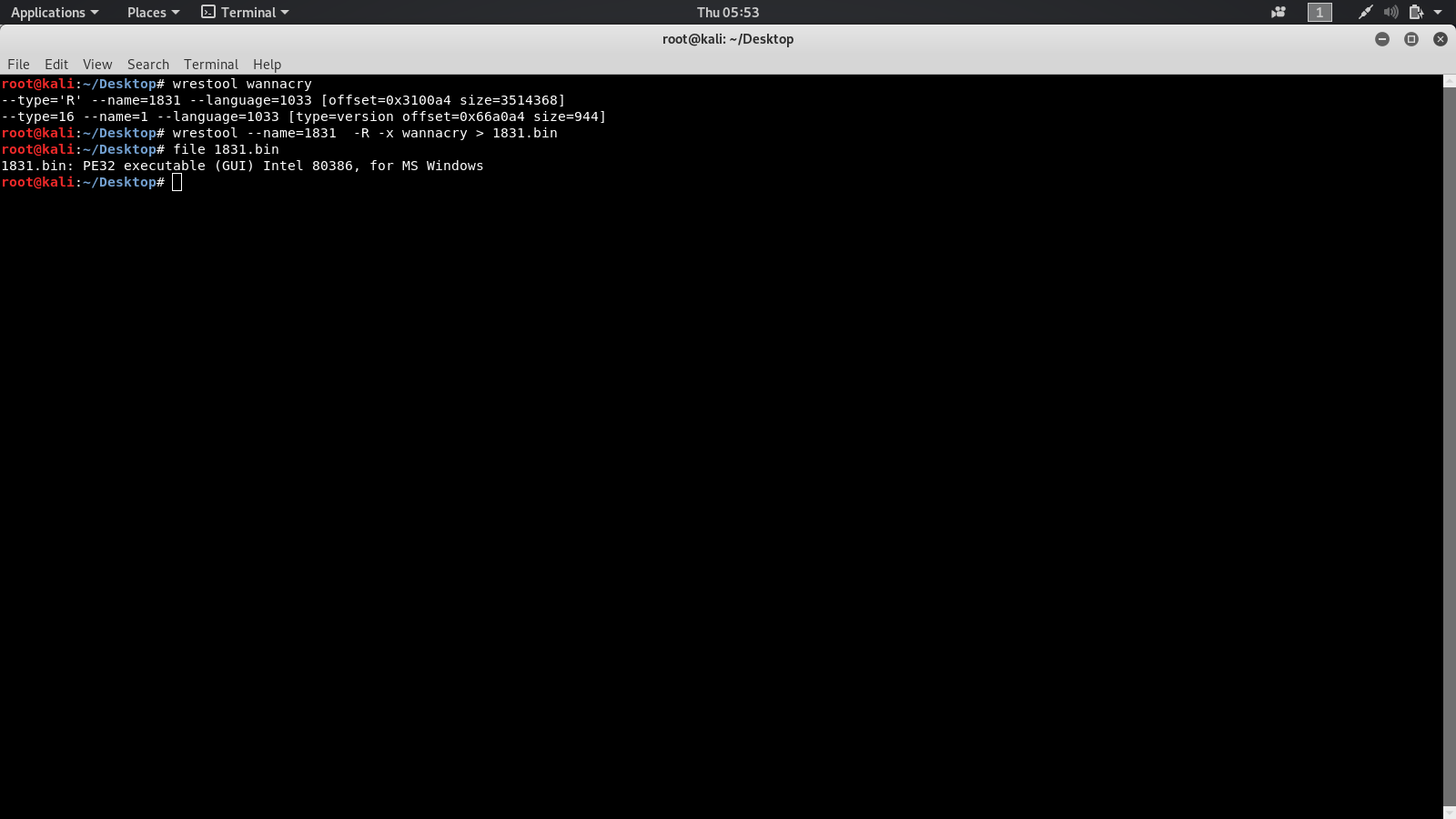
After getting the output you see that wrestool gave you a resource 1831 We just need to extract the resource so in order to do that type this command:
wrestool --name=1831 -R -x wannacry > 1831.bin
file 1831.bin
Now we need to analyze the 1831.bin file so drag and drop the file in ghidra
Here we need to start with the strings rather than function and after analyzing the strings go to function and analyze it
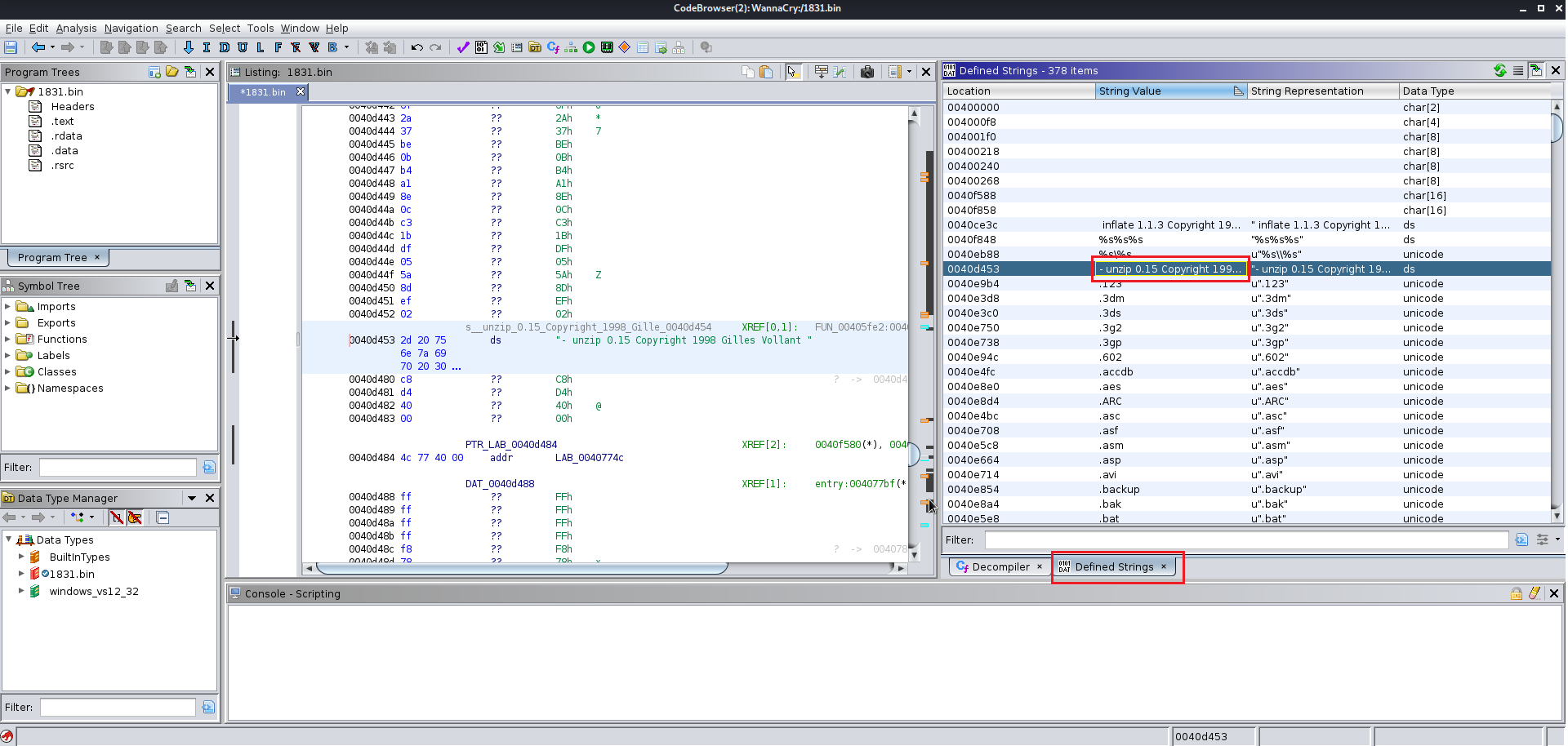
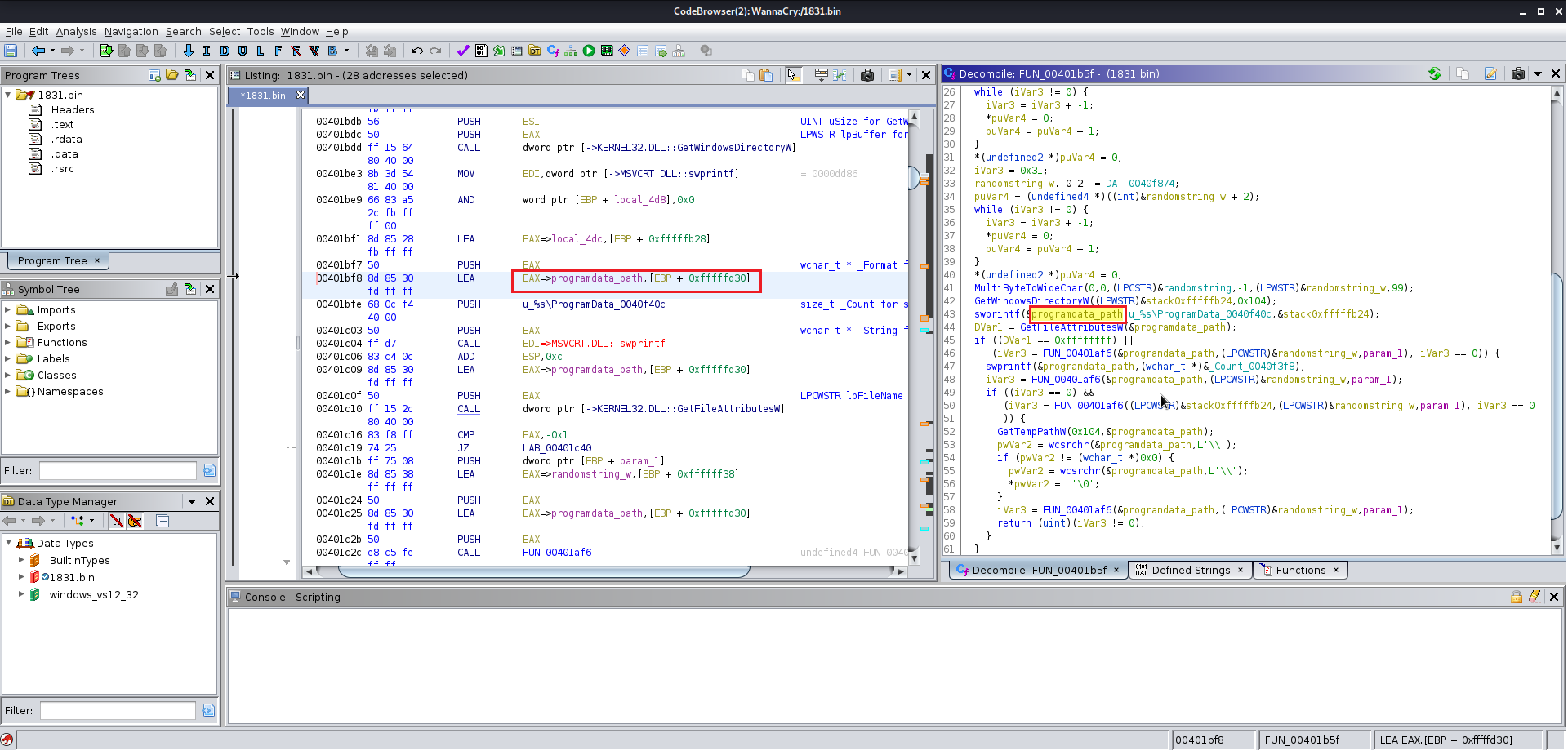
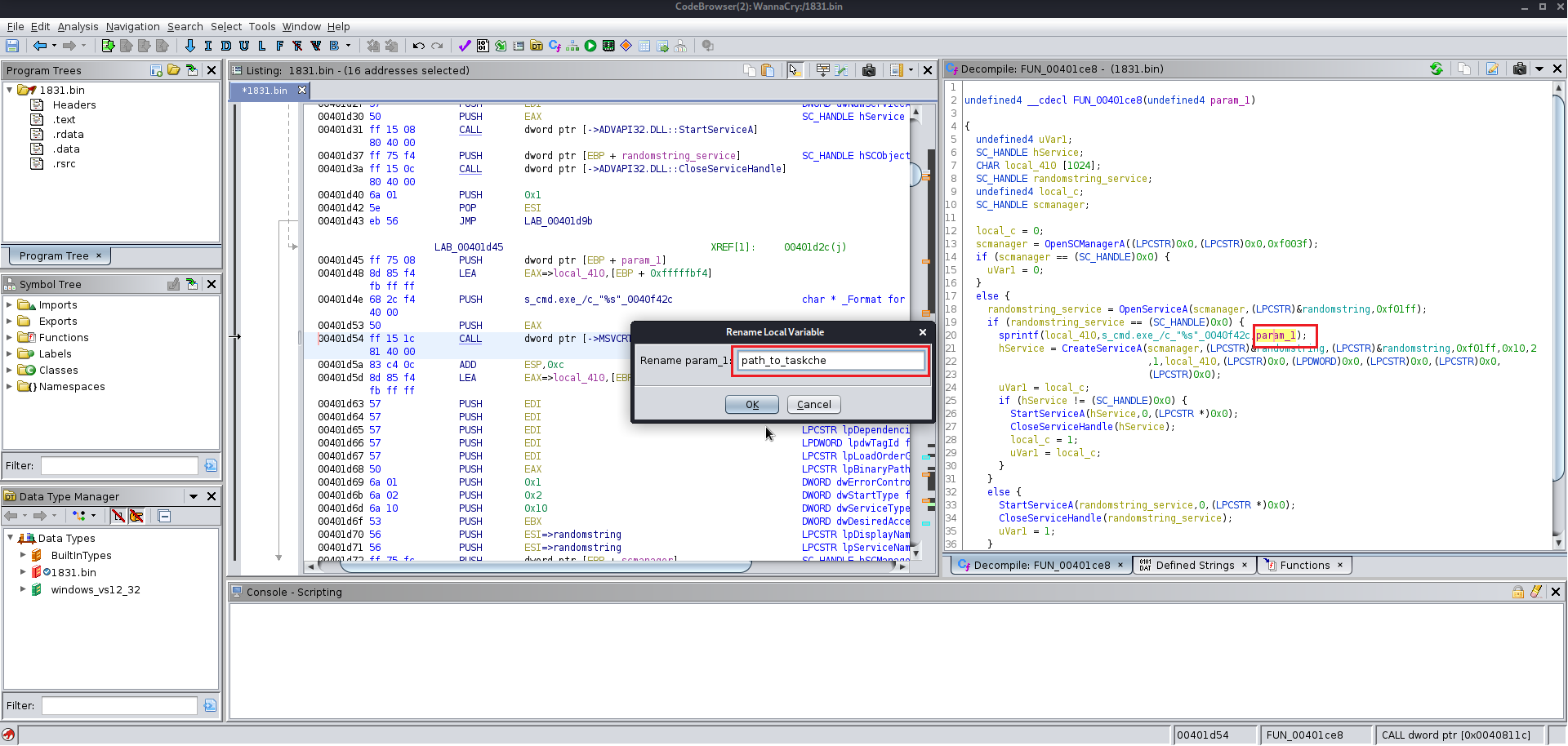
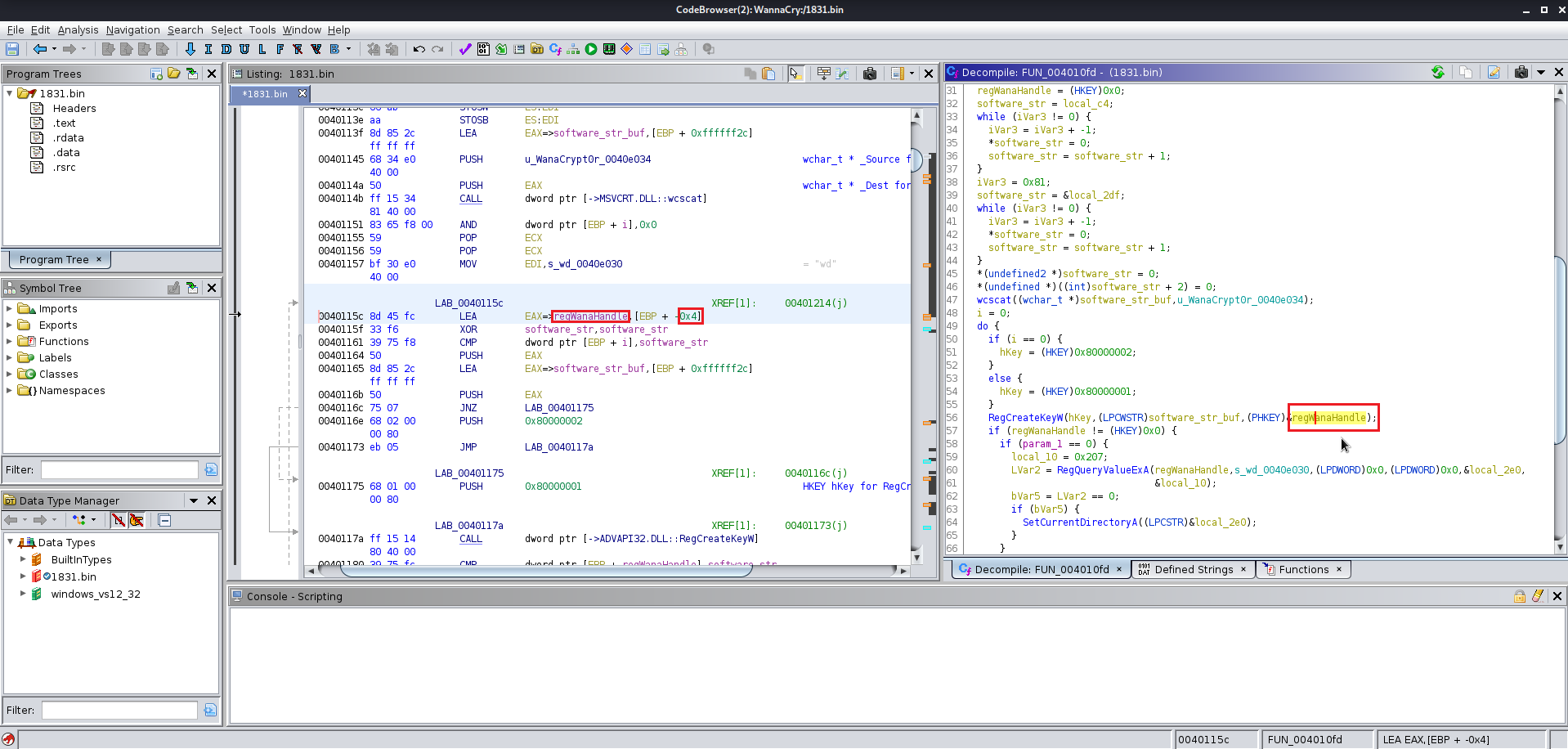
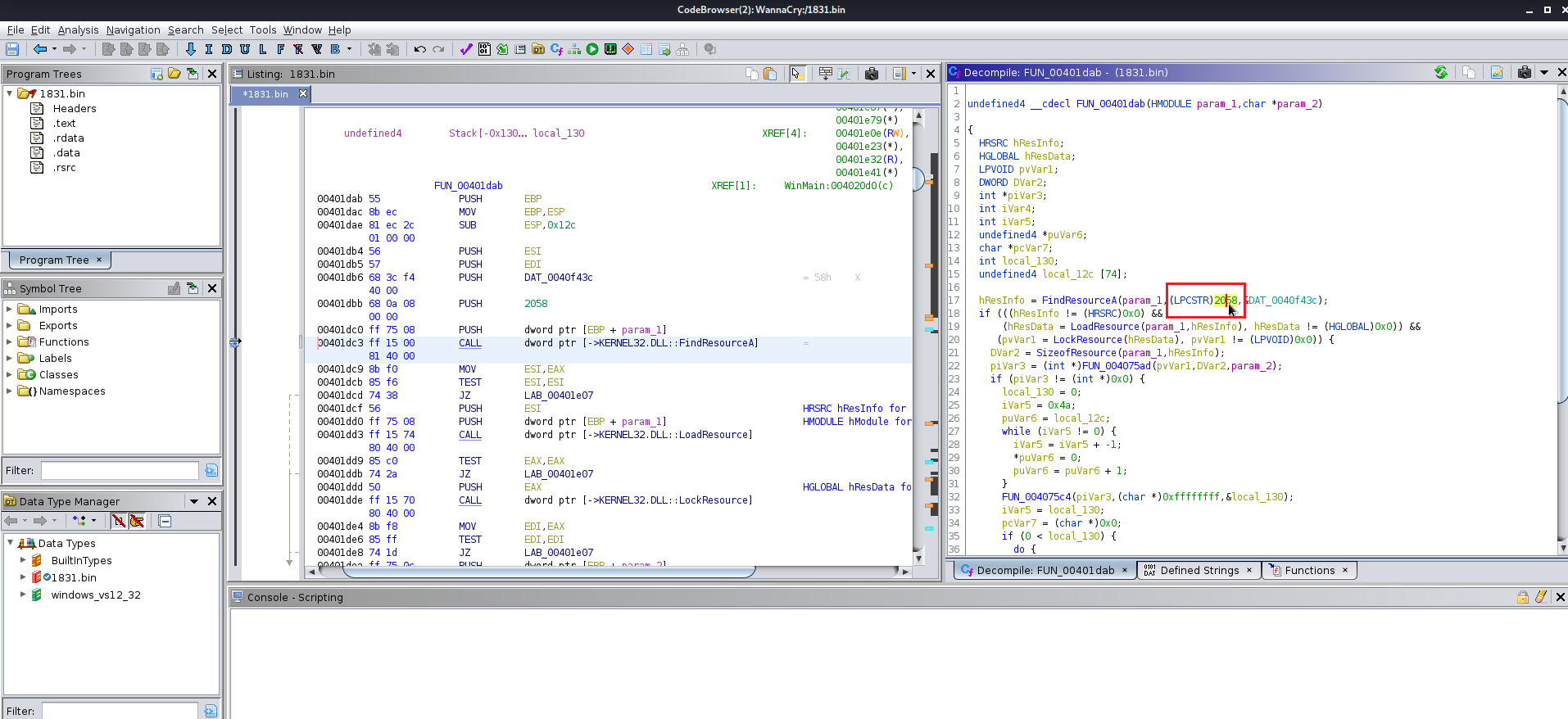
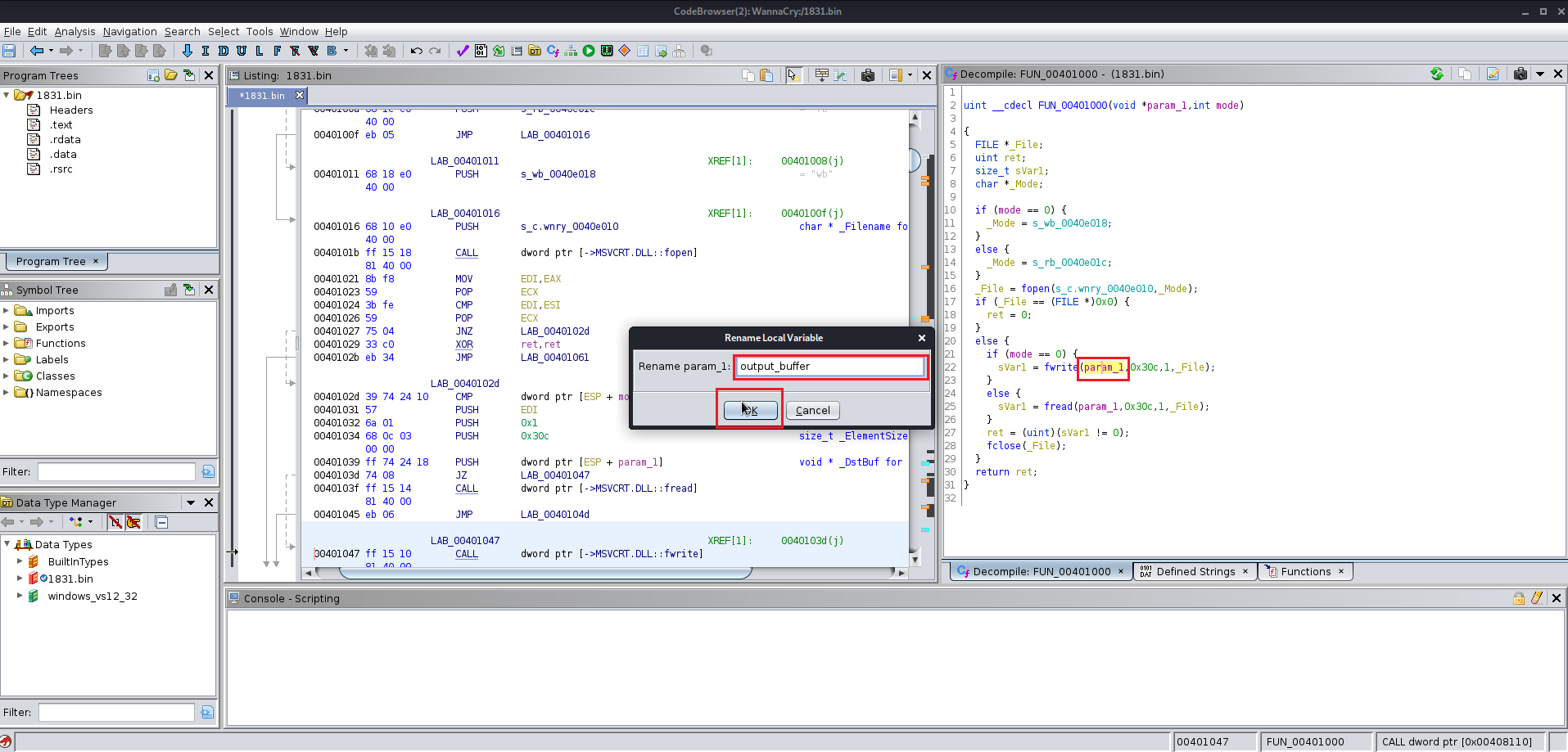
Now we need to analyze the 1831.bin file using wrestool
The commands are gonna be the same :
# wrestool 1831.bin
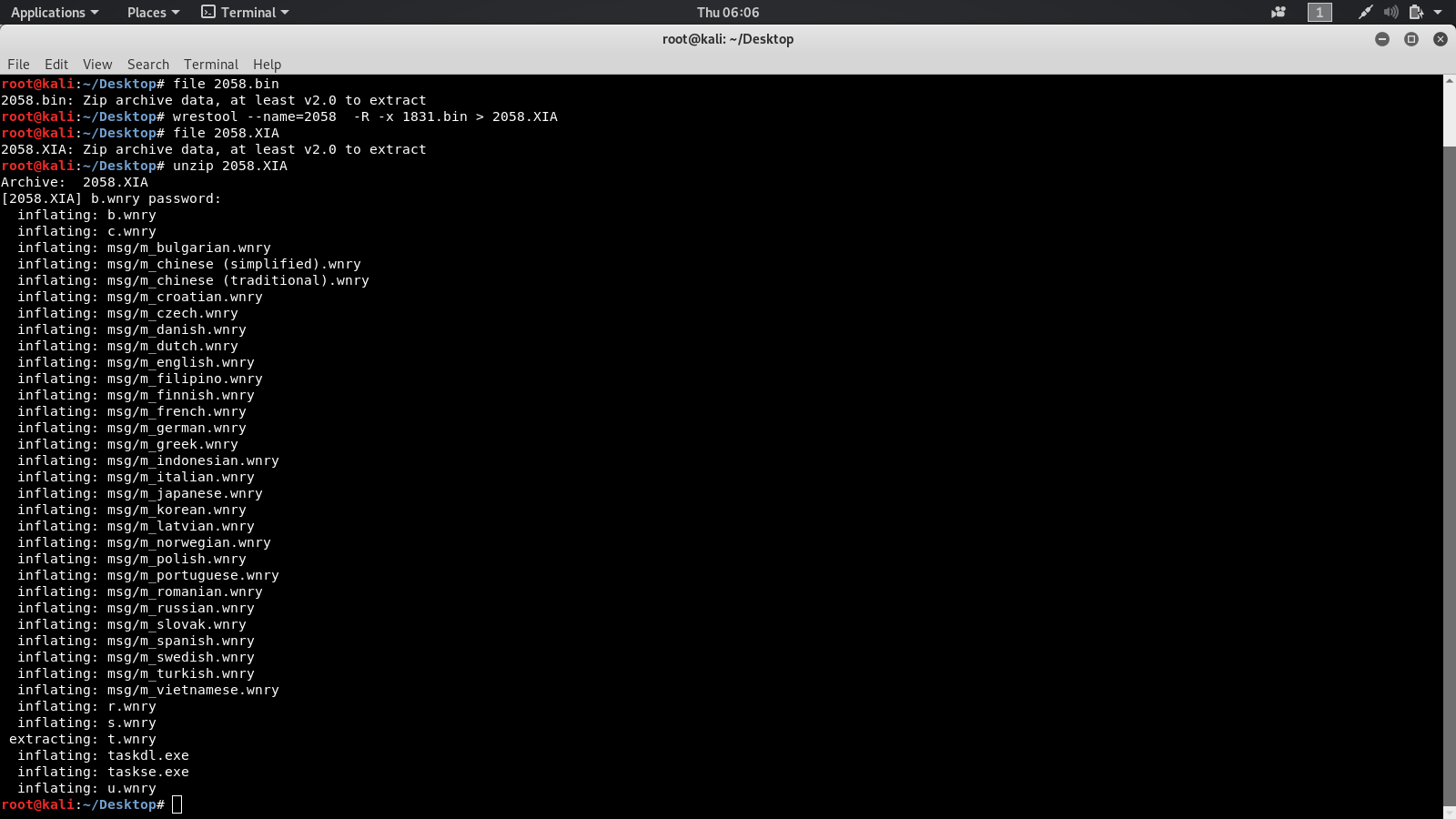
# wrestool --name=2058 -R -x 1831.bin > 2058.bin
# file 2058.bin
# wrestool --name=1831 -R -x wannacry > 2058.XIA
After this we need to unzip the file use command: # Unzip 2058.XIA
It will ask for a password so while analyzing the 1831.bin file using Ghidra You find that there was a strange string stored “WNcry@2ol7” try this as the password of the archive it will be extracted.
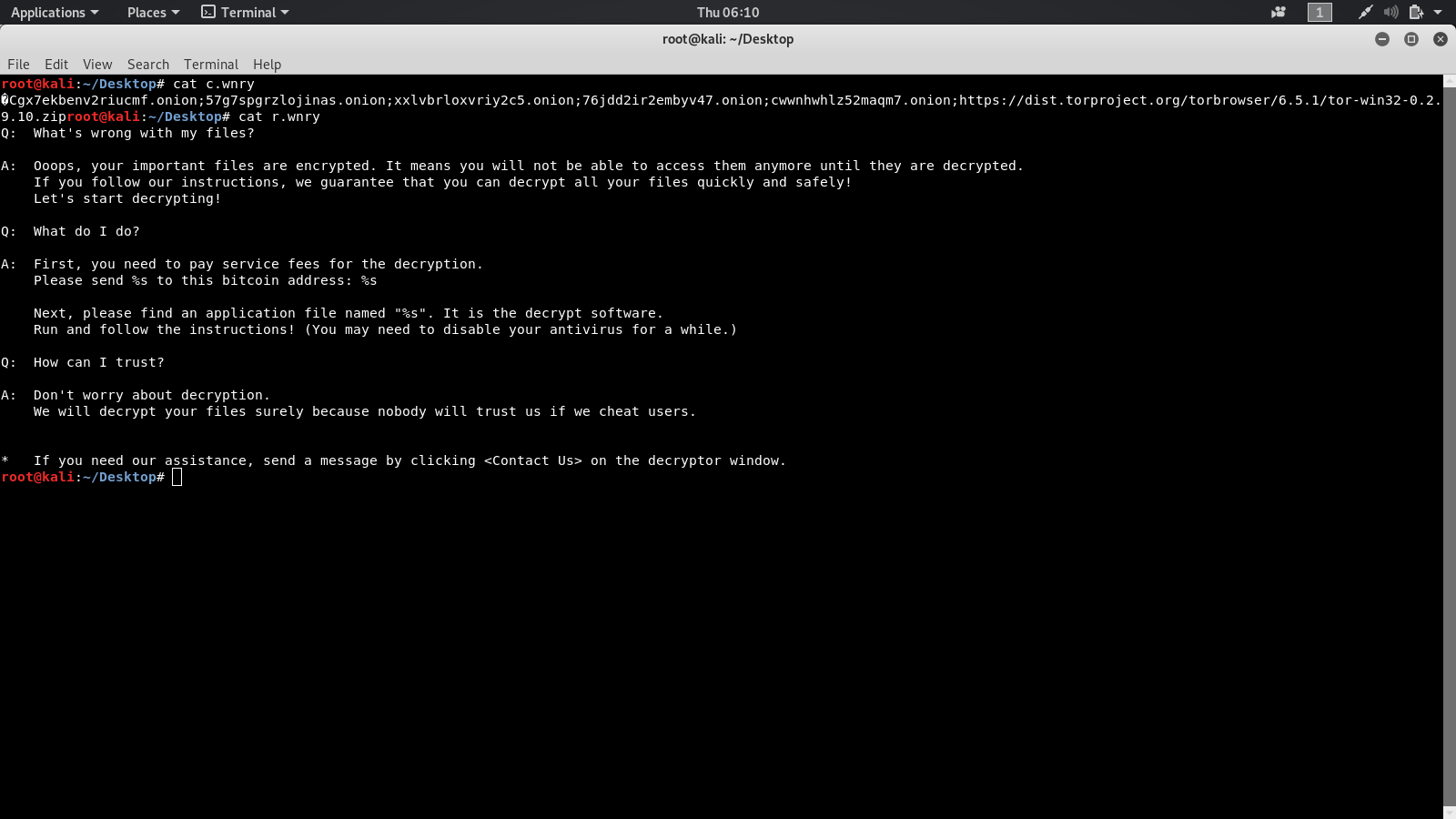
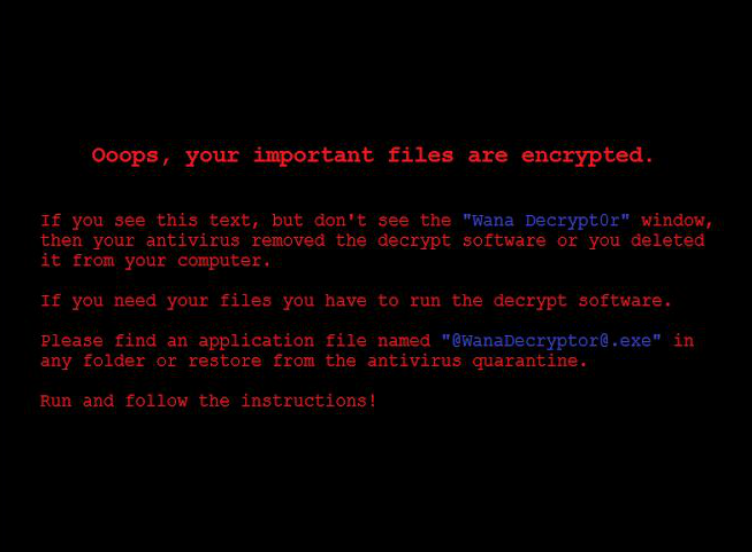
After you extract the files you will find vaiour images and txt files which are used in the infamous wannacry page.
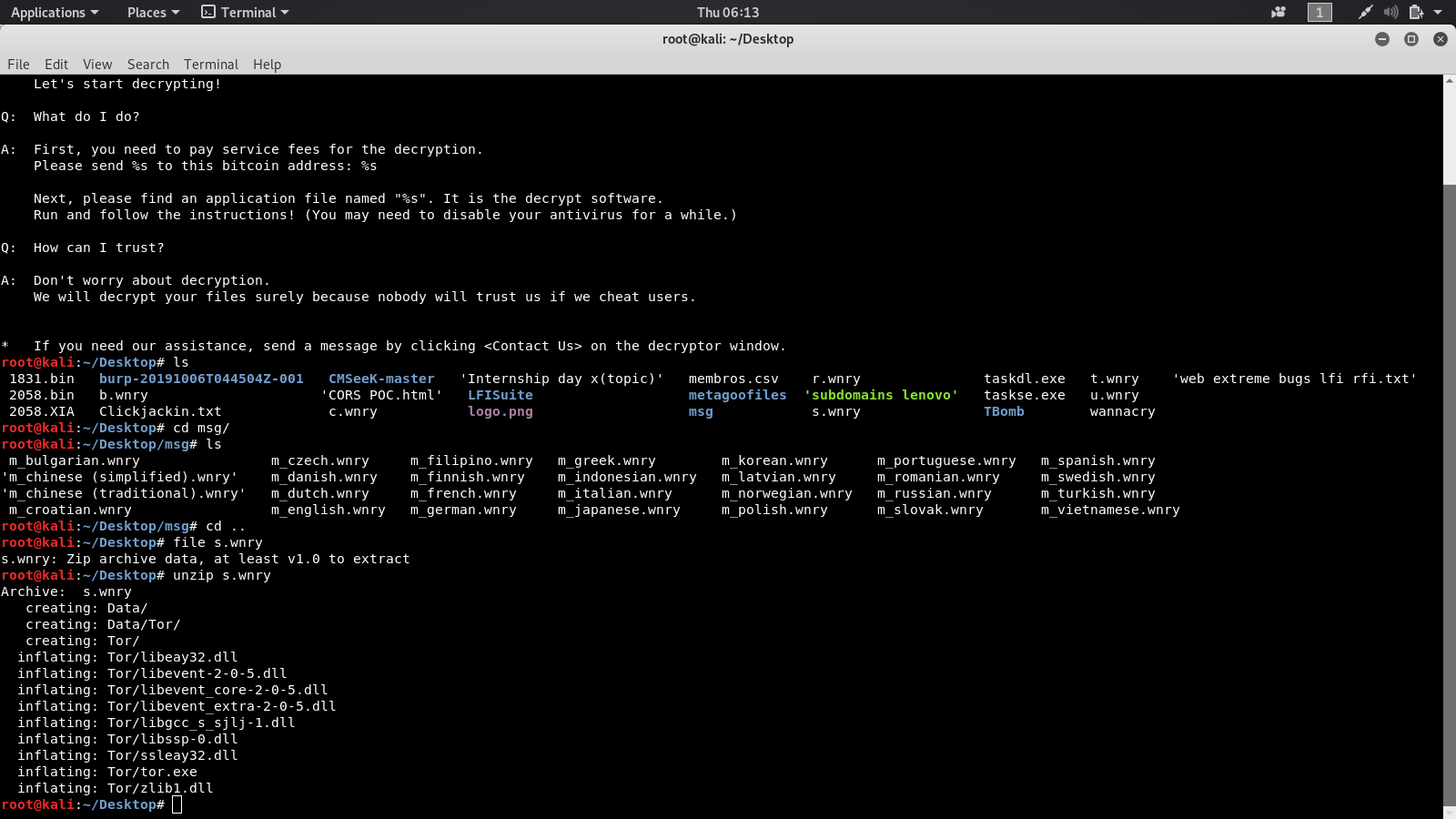
1. The versions befor 9.0.4 of Ghidra were rce exploitable using XXE > RCE
2. Ghidra always messes up your project by saving it as one of the temporary projects so you need to take a back up always.
Ghidra is one of the best tools out there to practice reverse engineering as it assists you by decompiling a lot of the information which is not achievable by a lot of the other reverse engineering tools.